
Web applications are a necessary tool for conducting business in today's connected world - common examples include online banking or retail websites. At the same time, these applications can be a significant liability to enterprise security. Using just one vulnerability in the public facing interface of a web application, an attacker can devastate a business.
Not only can an attack on a web application affect the back end systems and impact your organisation's compliance posture, it can also put your customer data at risk which can in turn cause a public relations nightmare.
Newly released mid-year Cyber Security Risks Report 2011 offers insights The HP 2011 mid-year edition of the bi-annual Top Cyber Security Risks report (bit.ly/hpentersec) features in-depth analysis on web application vulnerabilities and attacks using data from HP DVLabs, Application Security Center and Fortify security units as well as vulnerability disclosure data garnered from the Open Source Vulnerability Database (OSVDB). Key findings from this report include:
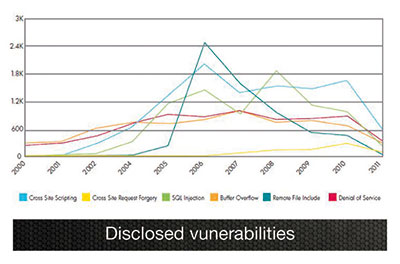
- The numbers of new vulnerabilities being reported is declining. There was a time when zero day attacks - exploits that leverage newly discovered vulnerabilities before they can be patched - were at an all-time high. However, this report shows an interesting and disturbing trend: the number of new vulnerabilities being discovered in commercial web applications is declining rapidly. OSVDB data reports just over 3000 new vulnerabilities disclosed from January - June 2011, which is down about 25% from the same time period last year.
- The number of vulnerabilities found in actual, production web applications is extremely high. At the same time, data from customer web application scans has shown the number of vulnerabilities found in these applications is still extremely high. For example, the Application Security Center Web Security Research Group (WSRG) conducted scans on 236 static web applications and found that 69% of these contained at least one SQL Injection vulnerability. What's more, 42% contained persistent cross-site scripting vulnerabilities. But if the numbers of new vulnerabilities disclosed is declining, where are these vulnerabilities coming from?
- Organisations aren't patching pre-existing vulnerabilities in commercial web apps leaving low hanging fruit for attackers to exploit; and/or
- There are a growing number of custom-developed web apps that are rife with vulnerabilities that can't be protected with commercially available security products.
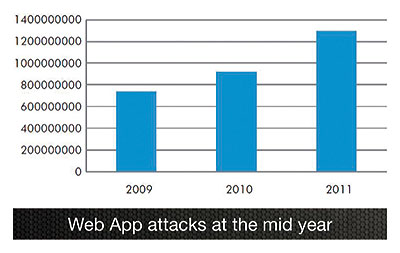
- The number of attacks on web applications is growing exponentially. HP DVLabs compiled attack data from its network of HP TippingPoint Intrusion Prevention Systems (IPS) to determine the danger these web applications vulnerabilities pose to information security. For 2011, attacks on web applications have increased by 26% over the same time period in 2010. Looking at all these data points together, it's clear that attackers simply do not need to rely on new web app vulnerabilities to launch their exploits. They are able to execute successful and profitable attacks using older information and techniques.
This report is intended for IT, network and/or security administrators that are responsible for securing the public facing communication with an organisation's customers, partners and employees. In addition to data on vulnerabilities and attacks, the report offers mitigation and risk management strategies for helping organisations address key business objectives including customer privacy concerns, service levels and compliance.
Download the full report here: bit.ly/hpentersec
What's your next enterprise security move?
Now that you've read about all of the most current risks and vulnerabilities, what do you need to do to protect your organisation from them? Get acquainted with HP's Enterprise Security Solutions here: bit.ly/hpesecsol
By Jennifer Lake, Security Product Marketing Manager, HP Networking
About HP Enterprise Security Solutions
HP Enterprise Security Solutions combines:
- An end-to-end approach to governing,
- Operating and optimising security practices
- The most advanced technology to automate remediation and proactively protect against the onslaught of modern security threats.
Working in conjunction with a wide spectrum of technology and service partners, HP's Enterprise Security Solutions are designed to reduce risk associated with financial loss, reputation damage, and audit/compliance requirements.
HP Enterprise Security Solutions provide a layered system of defence for the enterprise. HP can help you assess, transform, manage, and optimise across your risk strategy and security operations.