To this end, we decided to put Norton Internet Security 2012 through its paces, to see whether it would be our cyber security-gate of choice.
To start with, just like the previous version, Internet Security 2012 offered a quick, no fuss installation. Beyond entering our product code (the software allows for three licenses to be installed on separate PCs) and after a quick five minute installation, we were presented with a screen that reassured that we were now ready to start configuring our security settings.
Interface
To start with, Norton Internet Security 2012 offered up a clean, uncluttered interface divided into three sections: Computer Protection, Network Protection and Web Protection. Beneath this though, lay a well organised abundance of features.
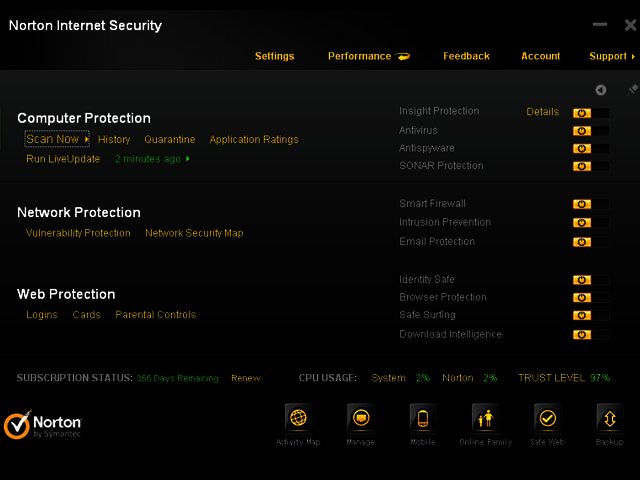
Under the computer protection section, common tasks such as initiating a scan, seeing our history, and which items had been quarantined, were front and centre. Additionally, features such as Insight protection, antivirus, and antispyware were also available. SONAR protection, which provides proactive real-time protection from unknown threats depending on the behaviour of applications, was also an option. All of the above could be turned on and off by sliding a switch on the interface, but by default all the features are turned on.
One of the particularly notable additions is the Insight feature. This gathers information from a worldwide online community and displays how many good files, bad files, and files still to be determined existed at a given time,. This was somewhat like having the online cyber-security version of the Central Intelligence Agency at our beck and call.
Network Protection
Under Network Protection, we were offered vulnerability protection from a staggering number of programmes that were known to be susceptible to attack. While Internet Explorer showed a not surprising count of 92 vulnerabilities, Windows XP topped the list with 140.
A network security map is also found here, which showed at a glance where and why our network wasn’t secured. Our wireless network was included in this – and if you’re one of those computer users who has not secured your wireless network with a security key, that would be revealed here, along with guidelines as to how to fix it.
By way of additional features, a rather self-explanatory smart firewall, intrusion prevention and email protection can also be enabled or disabled here.
Web Protection
Under this section, we were first tasked with setting up Identity Safe, a password protected feature which can store and protect sensitive information such as usernames, passwords, physical address and credit card numbers and then automatically fill these in as required.
Once done, we could then enter our log-in for protected websites, create information cards (such as credit card details) and set parental controls. Beyond this, the Web Protection feature also offered us the ability to enable browser protection (automatic protection from malware that exploits browser vulnerabilities) as well as safe surfing, which detects fraudulent websites and offers alerts when encountering a potentially fake site.
Under the hood
Digging a little deeper, we found that Internet Security 2012 had a number of very convenient extras that helped streamline our computing. The first of these was the option to see exactly which programmes were running at startup and stop them from loading when we booted our machine. This made a rather significant difference to our boot times.
Additionally, an activity monitor warned us when programmes were consuming large amounts of memory and detailed which programmes were the culprits. Another nice little touch is the discrete toolbar that rested in the upper right corner of our screen, and gave ready access to our activity map, management options, safe web feature and online backup (which requires setting up a Norton account).
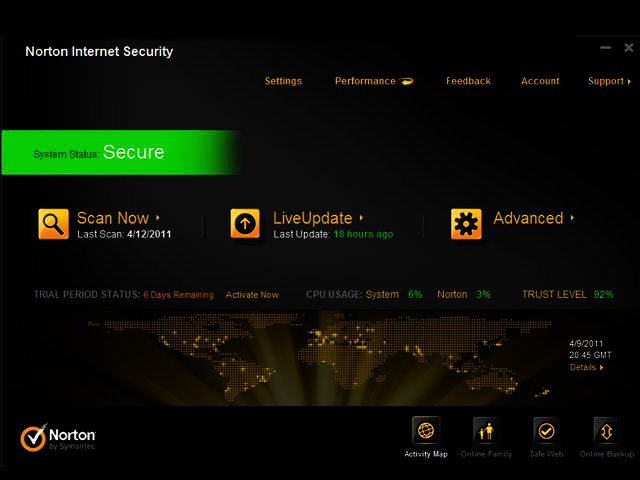
Performance
While there is some effort involved in taking advantage of all the features on offer, such as setting up the aforementioned account and setting up identity safe, this appeared to be the most demanding aspect of the software.
In other respects, it proved quick and responsive. Features opened without delay, while running a Quick Scan took an impressive six minutes. A full scan though would depend on the size of one’s hard drive/s and the number of files contained within, which would vary from one setup to the next. We were also heartened to see that the programme consumed only 16 MB of our RAM.
Scanning essentials
Possibly the heart of any security programme though is its scanning – an ability to scan and detect, and most importantly, clean any issues or malware from one’s system. Norton Internet Security 2012 offers several kinds of scans. The first of these is the computer scan, where we could either opt for a quick scan, a custom scan which only checks specified folders or a complete scan.
Additionally we were impressed to see that that we were also able to scan our Facebook wall (which doesn’t bode too well for the inherent security of the popular social network) for malicious links. This took just under two minutes to scan 67 links, and showed us a report of safe links, links that had warnings attached to them, caution on malicious links, as well as untested links.
Finally, we could further scan our ‘reputation’, which checked the trust level of all running processes and programmes on our machine.
As was expected, running full scans consumed considerably more processing power (up to around 80%), and for the purpose of this review, we opted to close programmes that we normally keep open, such as Skype, email and our browser, while performing these scans. Additionally, it can take a fair amount of time, depending on the number of files on your PC.
Once complete, you can then view the details of the scan, and see at a glance how many files were infected, how many infections have been resolved, which require attention, as well as the severity of the infection.
To the point
All in all, Norton Internet Security 2012 is a very comprehensive package. Features are logically accessible according to their functions, while there is enough depth to go beyond the surface and customise one’s security settings to one’s own preferences and personal usage patterns.
It managed to remain unobtrusive enough while providing valuable information. It neither hogged memory nor processing speed, with the exception of running full scans, and thus we concluded that it is a valuable, if not downright essential, addition to one’s PC security.
Although there is some work involved in getting the most out of it, for peace of mind and the imperative cyber security that comes with living in a digital age, we believe it is time well worth investing.
Looking for more Internet Security options? Check out all the 2012 packages here.
Pros
Feature rich
Accessible
Logically laid out
Licenses for three PCs
Cons
Does require some input to take full advantage of some features





